|
 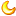 
- 帖子
- 1436
- 积分
- 1436
- 经验
- 1436 点
- 威望
- 43 点
- 金钱
- 2139 NG
- 魅力
- 2055
- 性别
- 男
- 来自
- 日本
- 注册时间
- 2003-5-15
 我们约会吧! 我们约会吧!
|
1#
 发表于 2003-5-25 11:55
发表于 2003-5-25 11:55
| 只看该作者
【原创】 ■有效指令■干扰指令■受静态反汇编干扰影响(可能夹杂有效指令)
随机变形解密代码一反汇编 随机变形解密代码二反汇编
00402399 E810100000 call 004033AE
......这里是待解密的数据
004033AE 33C0 xor eax,eax
004033B0 030424 add eax,[esp]
004033B3 4F dec edi
004033B4 81303A2FF76F xor dword ptr [eax],6FF72F3A
004033BA 8D927BFEB94B lea edx,[edx+4BB9FE7B]
004033C0 81EB1363BA05 sub ebx,05BA6313
004033C6 BE565A2628 mov esi,28265A56
004033CB B9FD632A4B mov ecx,4B2A63FD
004033D0 8D927999A372 lea edx,[edx+72A39979]
004033D6 50 push eax
004033D7 83042404 add dword ptr [esp],00000004
004033DB 58 pop eax
004033DC 81D1631AEA49 adc ecx,49EA1A63
004033E2 B9038FAC59 mov ecx,59AC8F03
004033E7 81309F0EC454 xor dword ptr [eax],54C40E9F
004033ED E802000000 call 004033F4
004033F2 81305E8D3411 xor dword ptr [eax],11348D5E
004033F8 45 inc ebp
004033F9 81C561DA8819 add ebp,1988DA61
004033FF 8DA877C07D6D lea ebp,[eax+6D7DC077]
00403405 81D172B86724 adc ecx,2467B872
0040340B 81D18250DA6F adc ecx,6FDA5082
00403411 40 inc eax
00403412 40 inc eax
00403413 40 inc eax
00403414 40 inc eax
00403415 BA05343E25 mov edx,253E3405
0040341A 81CEF3E8506D or esi,6D50E8F3
00403420 8D8EC925F813 lea ecx,[esi+13F825C9]
00403426 E802000000 call 0040342D
0040342B 81305E81EBDA xor dword ptr [eax],DAEB815E
00403431 CF iretd
00403432 56 push esi
00403433 5B pop ebx
00403434 BE6AB9C04F mov esi,4FC0B96A
00403439 8128C3FD8A44 sub dword ptr [eax],448AFDC3
0040343F 81EB6A1E5922 sub ebx,22591E6A
00403445 BA3F626473 mov edx,7364623F
0040344A 8D3411 lea esi,[ecx+edx]
0040344D 8D3411 lea esi,[ecx+edx]
00403450 81C5EFD40953 add ebp,5309D4EF
00403456 B961463A0D mov ecx,0D3A4661
0040345B 8D9F256D390F lea ebx,[edi+0F396D25]
00403461 83C004 add eax,00000004
00403464 8D8E768E543A lea ecx,[esi+3A548E76]
0040346A 8D9F18951E60 lea ebx,[edi+601E9518]
00403470 F7C24B08E427 test edx,27E4084B
00403476 8D8EA9DE097B lea ecx,[esi+7B09DEA9]
0040347C 8130F15CE20F xor dword ptr [eax],0FE25CF1
00403482 40 inc eax
00403483 40 inc eax
00403484 40 inc eax
00403485 40 inc eax
00403486 EB03 jmp 0040348B
00403488 817500BFF4CC66 xor dword ptr [ebp],66CCF4BF
0040348F 5F pop edi
00403490 8D3411 lea esi,[ecx+edx]
00403493 BFFE929765 mov edi,659792FE
00403498 8D8EE8981A6F lea ecx,[esi+6F1A98E8]
0040349E F710 not dword ptr [eax]
004034A0 81EBC190565A sub ebx,5A5690C1
004034A6 F7C204297F34 test edx,347F2904
004034AC 51 push ecx
004034AD 59 pop ecx
004034AE 83C004 add eax,00000004
004034B1 8D92191F1E3A lea edx,[edx+3A1E1F19]
004034B7 8D3C4B lea edi,[ebx+2*ecx]
004034BA 8128D2305C48 sub dword ptr [eax],485C30D2
004034C0 45 inc ebp
004034C1 8D8EB88DF60D lea ecx,[esi+0DF68DB8]
004034C7 81EB0DFBE501 sub ebx,01E5FB0D
004034CD 8D3411 lea esi,[ecx+edx]
004034D0 BFD5F8E40F mov edi,0FE4F8D5
004034D5 8D8E07E2C94A lea ecx,[esi+4AC9E207]
004034DB B969027870 mov ecx,70780269
004034E0 40 inc eax
004034E1 40 inc eax
004034E2 40 inc eax
004034E3 40 inc eax
004034E4 BD10E15748 mov ebp,4857E110
004034E9 81EBE13A5166 sub ebx,66513AE1
004034E9 81EBE13A5166 sub ebx,66513AE1
004034EF BD6877694C mov ebp,4C697768
004034F4 81CA5F4BD633 or edx,33D64B5F
004034FA 8D3C4B lea edi,[ebx+2*ecx]
004034FD 8DA8AE15EC3C lea ebp,[eax+3CEC15AE]
00403503 EB03 jmp 00403508
00403505 8175008100A6CB xor dword ptr [ebp],CBA60081
0040350C CB retf
0040350D 7E45 jle 00403554
0040350F E802000000 call 00403516
00403514 81305E83E8FC xor dword ptr [eax],FCE8835E
0040351A F7C26918A314 test edx,14A31869
00403520 EB03 jmp 00403525
00403522 8175004FE80200 xor dword ptr [ebp],0002E84F
00403529 0000 add [eax],al
0040352B 81305E4FBAF0 xor dword ptr [eax],F0BA4F5E
00403531 B695 mov dh,95
00403531 B695 mov dh,95
00403533 16 push ss
00403534 B9A7295A40 mov ecx,405A29A7
00403539 8100EA33A207 add dword ptr [eax],07A233EA
0040353F 40 inc eax
00403540 40 inc eax
00403541 40 inc eax
00403542 40 inc eax
00403543 BD10C73472 mov ebp,7234C710
00403548 51 push ecx
00403549 59 pop ecx
0040354A BB60F09B49 mov ebx,499BF060
0040354F C3 ret
00403550 0081F774CDE9 add [ecx-16328B09],al
00403556 16 push ss
00403557 CC int 03
00403558 CC int 03 00402399 E810100000 call 004033AE
......这里是待解密的数据
004033AE 8D857A2B1E5C lea eax,[ebp+5C1E2B7A]
004033B4 BF64BDA945 mov edi,45A9BD64
004033B9 BD1FC89D74 mov ebp,749DC81F
004033BE 33D2 xor edx,edx
004033C0 331424 xor edx,[esp]
004033C3 81D19B09281D adc ecx,1D28099B
004033C9 B93F342D54 mov ecx,542D343F
004033CE 8102B533B00B add dword ptr [edx],0BB033B5
004033D4 E802000000 call 004033DB
004033D9 81305E83EAFC xor dword ptr [eax],FCEA835E
004033DF 8D859220DF09 lea eax,[ebp+09DF2092]
004033E5 BD0844F628 mov ebp,28F64408
004033EA BD71563129 mov ebp,29315671
004033EF BD4673F473 mov ebp,73F47346
004033F4 51 push ecx
004033F5 59 pop ecx
004033F6 B839EC605E mov eax,5E60EC39
004033FB 8B0A mov ecx,[edx]
004033FD F7D1 not ecx
004033FF 870A xchg [edx],ecx
00403401 81F7371C9D3A xor edi,3A9D1C37
00403407 EB03 jmp 0040340C
00403409 8175008D3C4B83 xor dword ptr [ebp],834B3C8D
00403410 C2043B ret 3B04
00403413 C125F041487DEB shl dword ptr [7D4841F0],EB
0040341A 038175008D8E add eax,[ecx-7172FF8B]
00403420 E5A9 in ax,A9
00403422 7208 jb 0040342C
00403424 8D3C4B lea edi,[ebx+2*ecx]
00403427 25B8229170 and eax,709122B8
0040342C 81EBDC52B21A sub ebx,1AB252DC
00403432 8132EFAFAF62 xor dword ptr [edx],62AFAFEF
00403438 83EAFC sub edx,FFFFFFFC
0040343B 81F76E249432 xor edi,3294246E
00403441 8D8531114134 lea eax,[ebp+34411131]
00403447 B9EA77A92C mov ecx,2CA977EA
0040344C B94C2ADD26 mov ecx,26DD2A4C
00403451 81CE81810C09 or esi,090C8181
00403457 81EB0DE12535 sub ebx,3525E10D
0040345D 81F78492547E xor edi,7E549284
00403463 8B0A mov ecx,[edx]
00403465 F7D1 not ecx
00403467 870A xchg [edx],ecx
00403469 8D3C4B lea edi,[ebx+2*ecx]
0040346C E802000000 call 00403473
00403471 81305E81C566 xor dword ptr [eax],66C5815E
00403477 70A5 jo 0040341E
00403479 1881C5BA87D9 sbb [ecx-2678453B],al
0040347F 2B83C2048D9F sub eax,[ebx-6072FB3E]
00403485 86C5 xchg ch,al
00403487 1E push ds
00403488 56 push esi
00403489 81C51718B567 add ebp,67B51817
0040348F 8D3C4B lea edi,[ebx+2*ecx]
00403492 4F dec edi
00403493 BDF7932E1F mov ebp,1F2E93F7
00403498 810210711B3B add dword ptr [edx],3B1B7110
0040349E 83C204 add edx,00000004
004034A1 45 inc ebp
004034A2 BFBAB9843E mov edi,3E84B9BA
004034A7 8D853602AB72 lea eax,[ebp+72AB0236]
004034AD 8D9F68BC4942 lea ebx,[edi+4249BC68]
004034B3 BB27D6C218 mov ebx,18C2D627
004034B8 8D852C0C1B72 lea eax,[ebp+721B0C2C]
004034BE BEAC8EDF21 mov esi,21DF8EAC
004034C3 81322333FC25 xor dword ptr [edx],25FC3323
004034C9 81D1FB2EC64F adc ecx,4FC62EFB
004034CF 3BC1 cmp eax,ecx
004034D1 BB9CEB7719 mov ebx,1977EB9C
004034D6 BFB3BD6B47 mov edi,476BBDB3
004034DB 42 inc edx
004034DC 42 inc edx
004034DD 42 inc edx
004034DE 42 inc edx
004034DF 8D9F04650C0E lea ebx,[edi+0E0C6504]
004034E5 81C57A1D7837 add ebp,37781D7A
004034EB 8B0A mov ecx,[edx]
004034ED F7D1 not ecx
004034EF 870A xchg [edx],ecx
004034F1 81CE489C9153 or esi,53919C48
004034F7 45 inc ebp
004034F7 45 inc ebp
004034F8 BB5FAD5814 mov ebx,1458AD5F
004034FD 83C204 add edx,00000004
00403500 8132C178857F xor dword ptr [edx],7F8578C1
00403506 81EB871DEE00 sub ebx,00EE1D87
0040350C 2538858668 and eax,68868538
00403511 EB03 jmp 00403516
00403513 81750042424242 xor dword ptr [ebp],42424242
0040351A 4F dec edi
0040351B 81D1A3E2B055 adc ecx,55B0E2A3
00403521 81F7DCB8191C xor edi,1C19B8DC
00403527 BD1614994D mov ebp,4D991416
0040352C 8D3411 lea esi,[ecx+edx]
0040352F C3 ret
00403530 008D341181C5 add [ebp-3A7EEECC],cl
00403536 1E push ds
00403537 27 daa
00403537 27 daa
00403538 49 dec ecx
00403539 115159 adc [ecx+59],edx
0040353C BB6CAFEC5B mov ebx,5BECAF6C
00403541 BFC207D31B mov edi,1BD307C2
00403546 81D15A25C561 adc ecx,61C5255A
0040354C CC int 03
0040354D 9B wait
0040354E 49 dec ecx
0040354F C3 ret
00403550 0081F774CDE9 add [ecx-16328B09],al
00403556 16 push ss
00403557 CC int 03
00403558 CC int 03
00403559 CC int 03
0040355A CC int 03
0040355B CC int 03
注解: 注解:
Rnd Reg=eax Rng Reg=edx |
|